How to enable self-sign-up
This guide walks you through the steps to enable self-sign-up of users. PhariaAI uses Zitadel as an identity provider. Zitadel provides a self-service registration flow that allows users to sign up for an account without the need for an administrator to create an account for them. Using this flow, a user can sign up for an account by providing their email address and a password. They will then receive a verification email to confirm their email address and complete the registration process. We recommend to filter the email addresses to only allow users with a specific domain to sign up.
Prerequisites
- You enabled the flag
pharia-iam.config.adminEnableZitadelManagementduring the installation of PhariaAI, see section 1 at Installation of PhariaAI -> Helm Chart Installation -> IAM Configuration. If you are running PhariaAI version 0.3.145 or lower: You have installed PhariaAI with an extra Zitadel admin account, see section 1 at Installation of PhariaAI -> Helm Chart Installation -> IAM Configuration. - You have an email provider which you can use to send verification emails.
Configure an Email Provider in Zitadel
To enable self-sign-up, you need to configure an email provider in Zitadel. This is necessary to send verification emails to users who sign up for an account. You can use one of the pre-configured email providers or any other email provider that supports SMTP or API-based email sending.
- Open the Zitadel Console
- Navigate to the Zitadel Console at
https://login.<YOUR_CONFIGURED_DOMAIN>/and log in with your initial user account. (Use the extra Zitadel admin account you configured before installation if you are using Pharia IAM version 0.8.55 and lower.) - If you happen to land on the info page of your admin account, navigate to
https://login.<YOUR_CONFIGURED_DOMAIN>/ui/consoleor click on the Zitadel logo in the top left corner. If this has no effect, you probably logged in with the wrong account.
- Navigate to the Zitadel Console at
- Configure an Email Provider
- Open the
Default Settingson the right upper corner and navigate to theEmail Providerssection. - Add your preferred email provider by clicking on its icon and following the instructions.
- Open the
Enable self-sign-up in Zitadel
- Open the Zitadel Console
- Go back to the main screen by clicking on the Zitadel logo in the top left corner.
- Enable Self-Sign-Up and Domain Discovery for the Pharia Organization
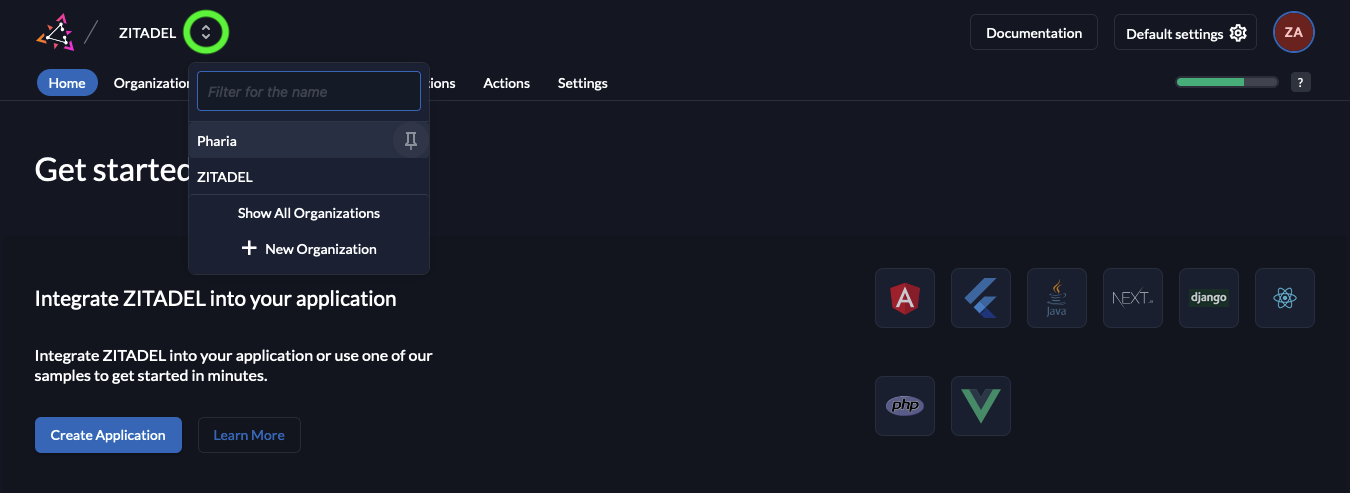
- Switch to the Pharia Organization by clicking on the two arrows next to the organization name in the top left corner and choosing the Pharia Organization.
- Go to the
Settingstab and selectLogin Behavior and Security. On the bottom of the page, check the boxes forUser Registration allowedandDomain Discovery allowed. Then click onSave.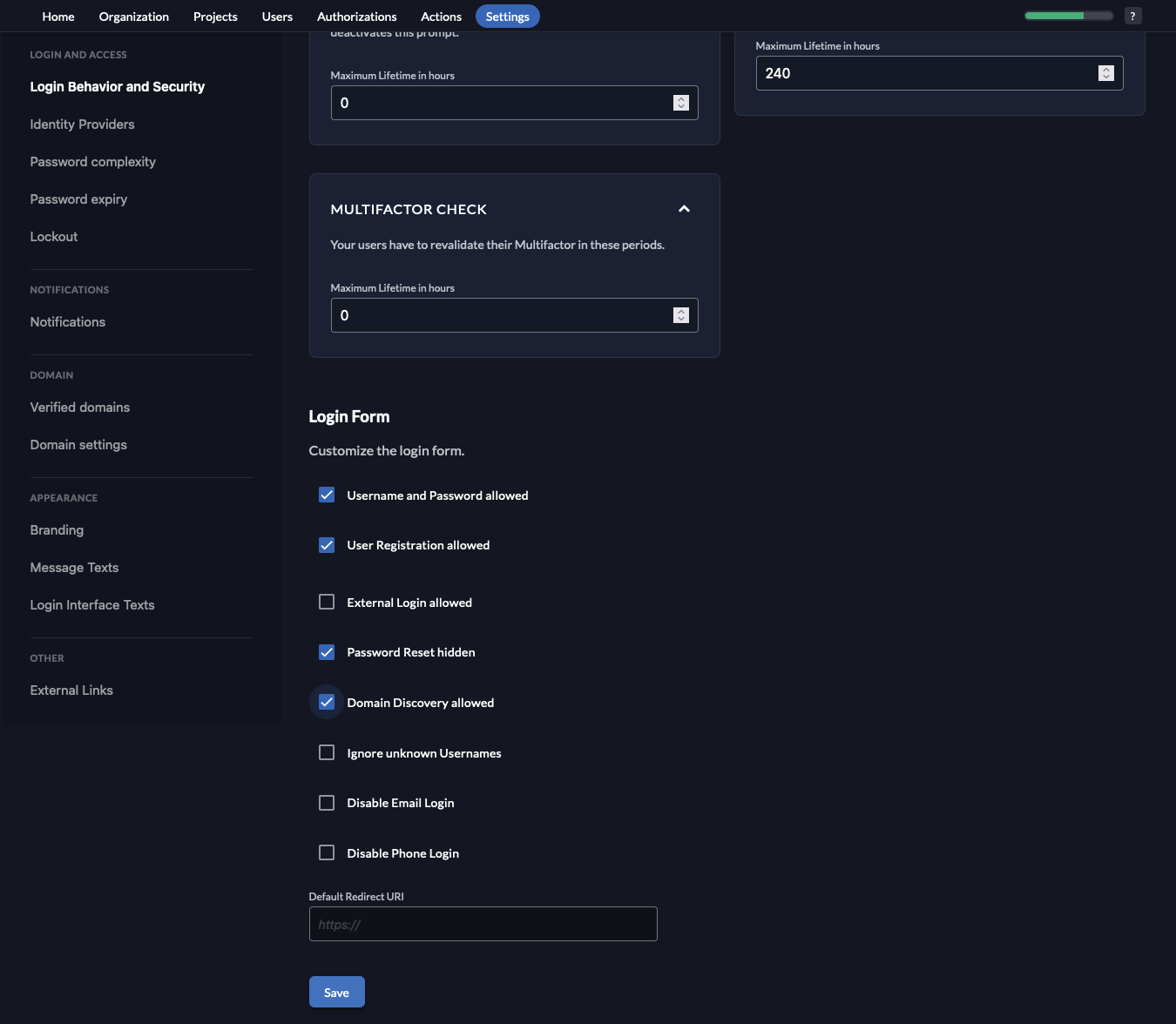
- Navigate to the settings for
Verified domains. Make sure that the email domain of your company appears here, otherwise add it by clicking on the+ Newbutton.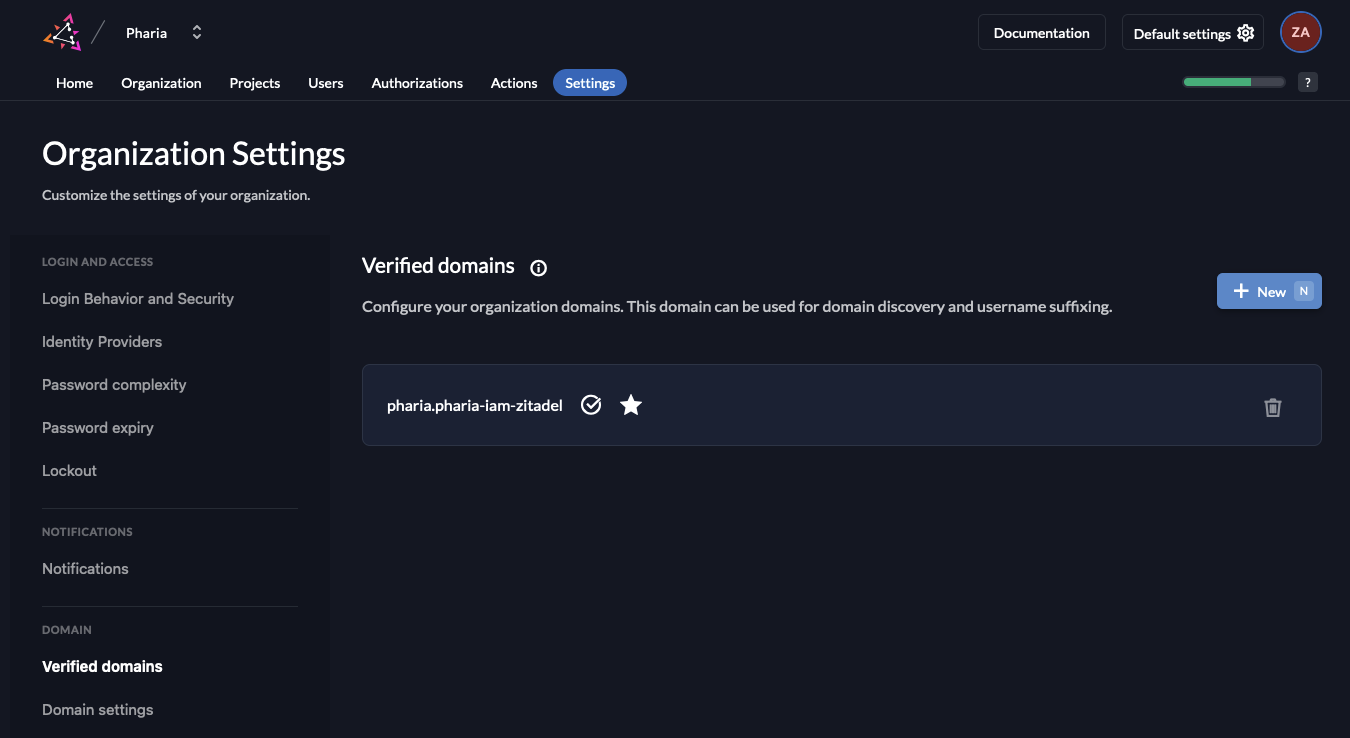
- Switch to the Pharia Organization by clicking on the two arrows next to the organization name in the top left corner and choosing the Pharia Organization.
- Install check for correct domain on sign up
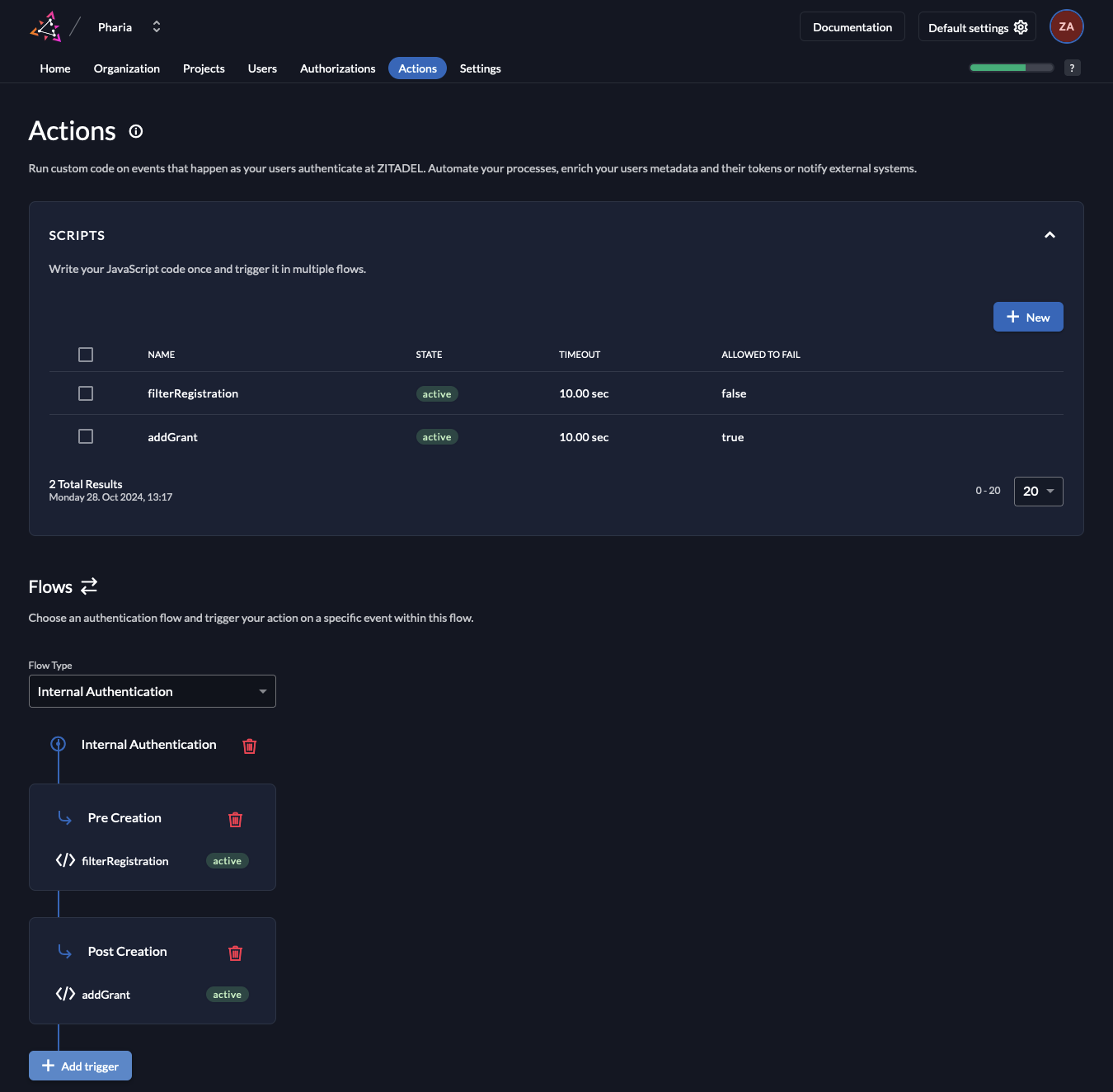
- Navigate to the
Actionstab and click on the+ Newbutton to create a new action. Name the actionfilterRegistration. Copy the code from the snippet below and paste it into the editor. You need to replace<VerifiedDomain>with the domain you want to allow for sign-up. You can also adapt the code to allow multiple domains. For further information on how to write actions, see the Zitadel documentation./**
* Only allow users with a given domain to register
*
* Flow: Internal Authentication or External Authentication, Trigger: Pre creation
*
* @param ctx
* @param api
*/
function filterRegistration(ctx, api) {
if (!ctx.v1.user.human.email.endsWith("@<VerifiedDomain>")){
throw "email needs to be from domain '<VerifiedDomain>'"
}
} - Disable the box
Allowed To Fail. Disabling this checkbox generates a warning as any coding errors for example may now prevent anyone to register. However, as we specifically want to prevent registration from users with an invalid domain. Therefore, we can close the warning and then click onAdd.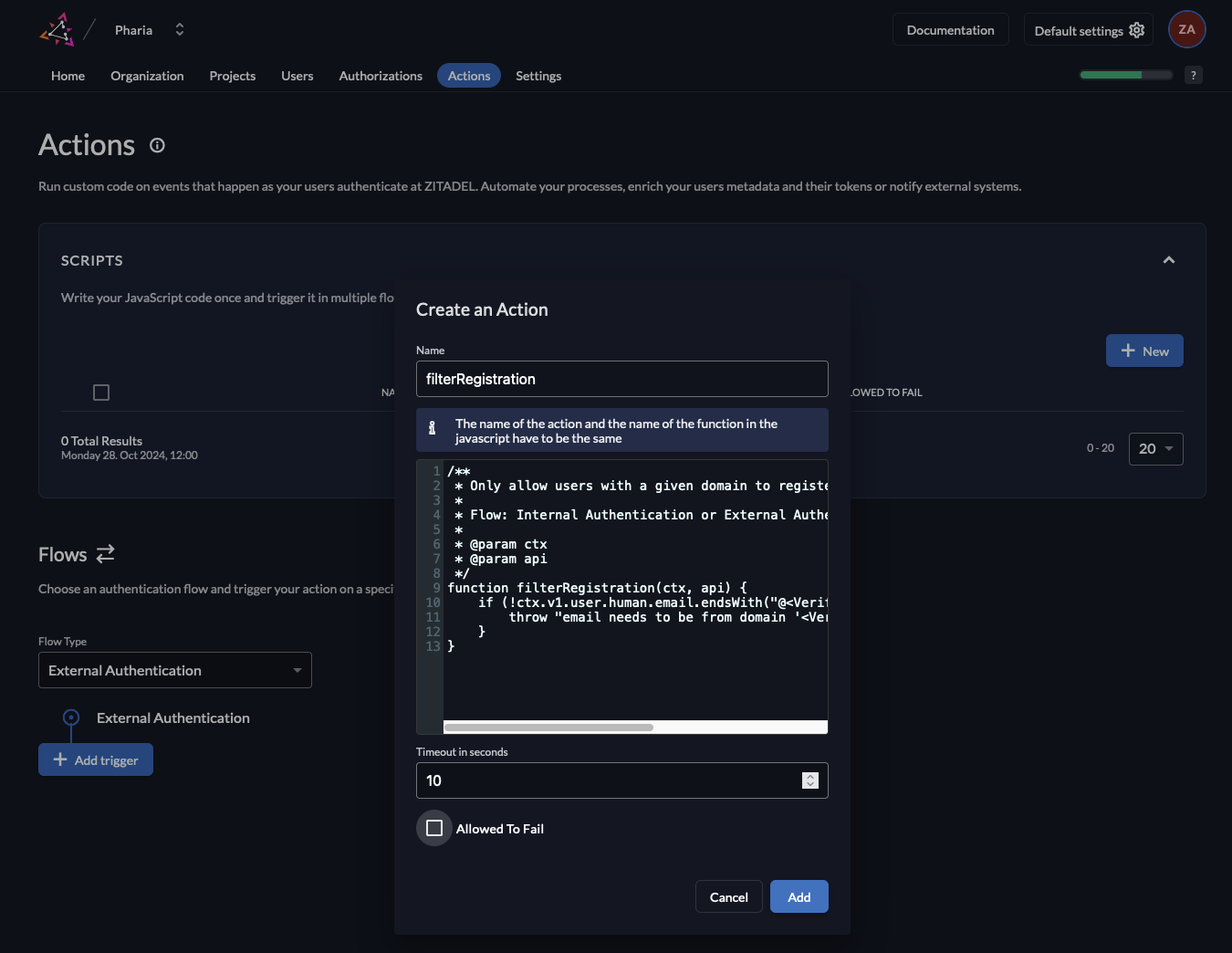
- Select the Flow Type
Internal Authenticationand click theAdd Triggerbutton. Now select the Trigger TypePre Creationand select the previously created Action. Click onSave.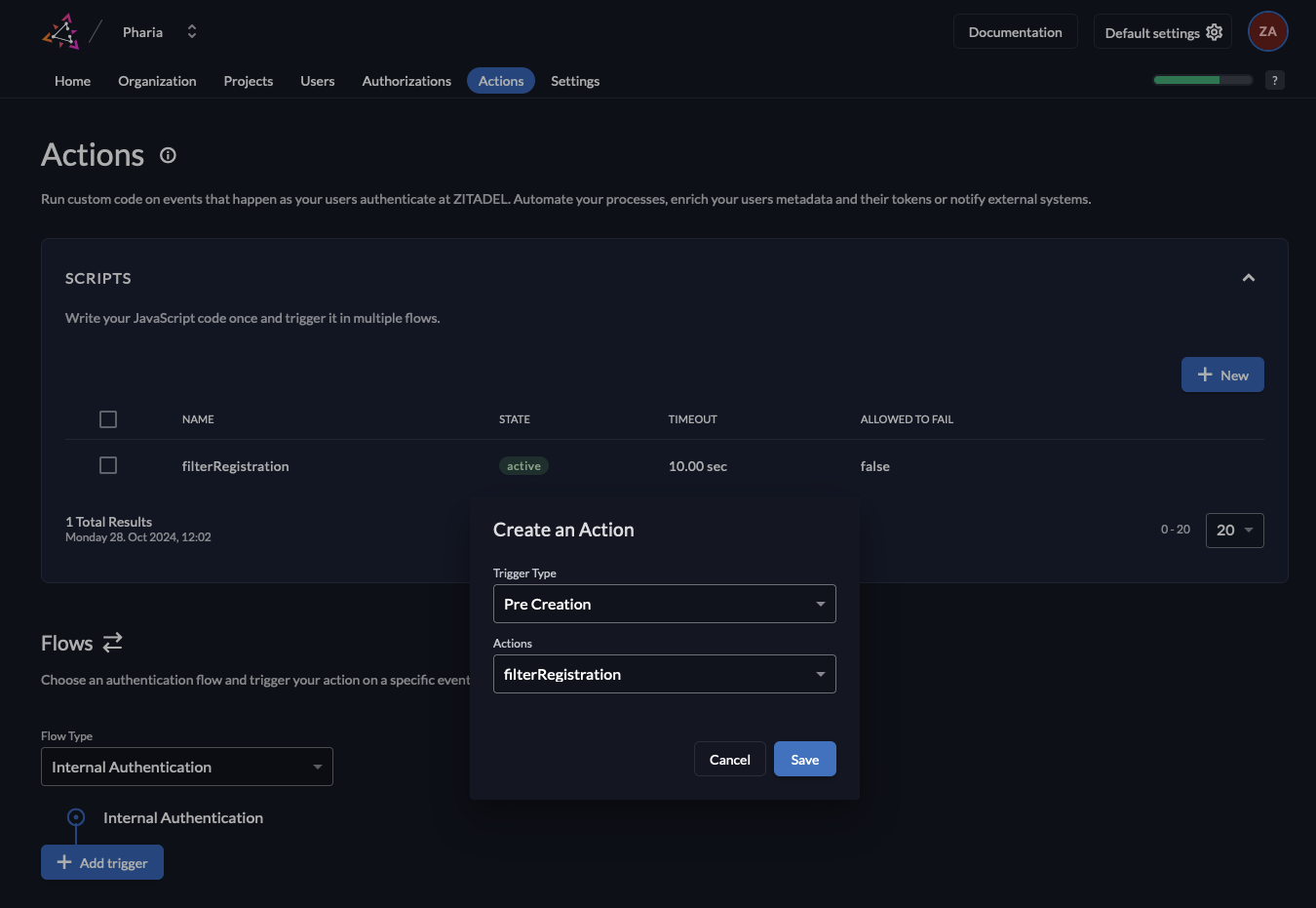
- Navigate to the
Optional: Configure Default Roles for self-sign-up
A user needs a role in order to access any resource in PhariaAI. You can configure default roles for users who sign up for an account. If you don't, an admin will need to assign roles to users manually. However, care should be taken when assigning roles to users automatically, as this can lead to security risks (not every user should have admin rights for example).
Add Role Assignment
- Stay in the
Actionstab for the Pharia organization and add another Action with the nameaddGrantand the code from the snippet below. The boxAllowed To Failthis time is optional. Then, click onAdd./**
* Add a usergrant to a new created/registered user
*
* Flow: Internal Authentication or External Authentication, Trigger: Post creation
*
* @param ctx
* @param api
*/
function addGrant(ctx, api) {
api.userGrants.push({
projectID: '<the projects resource ID>',
roles: ['<the role key>']
});
} - Again, select the Flow Type
Internal Authenticationand click theAdd Triggerbutton. This time select Trigger TypePost Creationand select the previously created Action. Click onSave.